Gmail Accounts Hacking Risk 2012!
Millions of users use Gmail as their information center to perform actions such as Business, Chat, Place Orders, Payment confirmation, main password recovery mail for different web services and so on...
many people - including myself use Gmail to store and save important and personal data, none of us want our data to be at risk of steal, manipulation, and obviously not considering the Gmail account being completely hacked!
I found a possibility to do all that!
Fortunate enough for us, Google is taking a lot of efforts securing their services. mostly by doing a great job, which integrates supporting a vulnerability reward program.
I made a quick research and reported this vulnerability along with all the related details.
I must say Google's response was very quick and so as their fix. (it is Fixed)
as it appears here :Vulnerability Reward Program even after the bounty raise:
Google's Reward for this bug: $1337 (mail.google.com)
PoC Picture:
Technical Details:
I am quite busy at work and personal life at these days so I placed a side the reward programs of Google, Facebook And others.
many people - including myself use Gmail to store and save important and personal data, none of us want our data to be at risk of steal, manipulation, and obviously not considering the Gmail account being completely hacked!
I found a possibility to do all that!
Fortunate enough for us, Google is taking a lot of efforts securing their services. mostly by doing a great job, which integrates supporting a vulnerability reward program.
I made a quick research and reported this vulnerability along with all the related details.
I must say Google's response was very quick and so as their fix. (it is Fixed)
as it appears here :Vulnerability Reward Program even after the bounty raise:
Google's Reward for this bug: $1337 (mail.google.com)
PoC Picture:
Technical Details:
I am quite busy at work and personal life at these days so I placed a side the reward programs of Google, Facebook And others.
I was just checking my mail the other day and I noticed something different.
Google made this nice change in Gmail , apparently around December 2011 - Google Adds circles to Gmail
"Users can now Filter their Mails based on their Circles"
Trusting your Google+ Friends?
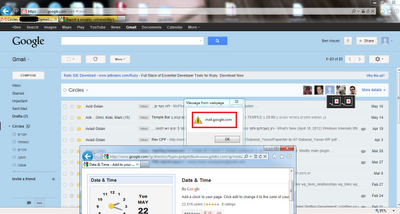
When I clicked this Gmail Circles feature, I saw my Google+ connections: profile pictures, nicknames and some other circles related data
Do they Control this data?! - Yes!
I had to spend some time back in the business, Gmail Stored XSS is a serious finding!
So I imminently researched that feature's JavaScript code.
It appeared that data that comes from Google+ was not sanitized by Gmail!
It appeared that data that comes from Google+ was not sanitized by Gmail!
zk.prototype.Ca = function $pn(a, c, d) { this.xa = 0;
if (!this.ea) { //Shorten/removed var e = this.Bb.zb().body, g = this.ea.va(); //Shorten/removed
e.wa = h } a: { if (d) switch (d.toLowerCase().split(",")[1]) { case "l": break a; case "r": /removed; break a } e = 2 } this.wa.setPosition(cka(d), e, i, -1); jc(this.ea.va(), "T-ays-avH"); ud(this.ea.va(), 0, 0); this.ea.Mc().innerHTML = c; //c = Data from Google+; this.wa.To(a); this.wa.Me(k, 0) };
This Gmail Code was creating a Tool-tip that Included profile circles information that comes from your Google Plus friend's account, if they used a payload, your mail account would have been at a serious risk.
Exploiting the Vulnerability - malicious Google+ Account.
As First it is important to note that Anyone that already got accepted as your friend in Google+ could trigger this attack on your Gmail account!
So all that is left is crafting a very nice Google+ account with some attractive profile, then after this evil account gets many friends/victims - Attack em all!
Google+ was and still is blocking the possibility of using a payload in the required field that was used to trigger this attack, but I found a way around it, sorry but I cannot reveal how I did that. (I am sure some of you pros might know how).
After I used my technique and crafted the Google+ evil profile it was possible to attack Gmail of all of that profile's friends!
PoC Picture:
As always I appreciate the opportunity to preserve my skills and gain some more experience
Thank you Google security team.
"Ben Hayak" - Google Security Hall of Fame Page
http://www.google.com/about/company/halloffame.html
PoC Picture:

Thank you Google security team.
"Ben Hayak" - Google Security Hall of Fame Page
http://www.google.com/about/company/halloffame.html

Great work ...
ReplyDeleteYour post is meaningless and pointless, except to brag. You've provided no proof and refuse to publish your work. This is not how disclosure is meant to work. If Google has "fixed" the issue as you suggest, your workaround used to bypass their filters can be disclosed.
ReplyDeleteYour hacking is bad, and you should feel bad.
Satish b, Thank you.
ReplyDeleteAnonymous,
first of all,
there is a proof which is a screen shot with date & most important, the vulnerable code is in here in javascript, the fact that you cannot read javascript good enough to see it's vulnerable is your own problem.
second of all I respect Google Security team and never said they fixed my bypass or methods(up to the day this was posted or maybe up to today), I only confirmed they fixed the XSS, so stop crying and deal with it.
I don't think you would have posted as Anonymous if you were in any position to criticize my work, I think you are the one that feels bad jealously?. ;)
Very nice find. Stored XSS vulnerabilities are particularly nasty and given that this one works via a trust relationship, it was even more likely to be a successful attack vector.
ReplyDeleteNice work.
ReplyDeleteits cool dude.
ReplyDeletefound a permanent xss accidentally,you are full of luck,more,its on google! :D
congratz
Nice find!
ReplyDeleteThat's the kind of flaw that deserve more than $1337. Google should have paid more for this one.
Thank you Mario, I do agree,
ReplyDeletebut, I did enjoy posting about it.
and this article of course:
http://www.nypost.com/p/news/business/white_hat_cyberbug_bounty_nets_cash_7c6JPTUlEmoDBsszeD6c1I
Nice :) I just found me to a XSS but non-persistent in google.com :) and i just got 1.337 $ xD
ReplyDeleteIf you want a picture you can tell me :) Thanks
I'm on hall of fame !
Darius
I forgot something ... i just found XSS in [subdomain].adobe.com ... if i will report it will give me something ? thanks again !
DeleteThanks a lot on this great information and ideas..
ReplyDeleteI got a confirmation mail from google . But My name is yet to be updated any idea when it would be done
ReplyDeleteThis is very nice blog and informative. I have searched many sites but was not able to get information same as your site. I really like the ideas and very intersting to read so much and Please Update and i would love to read more from your site
ReplyDeleteThanks
This comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDelete